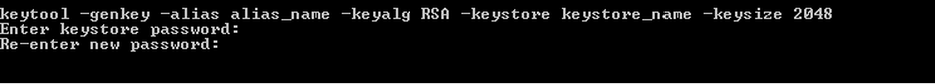
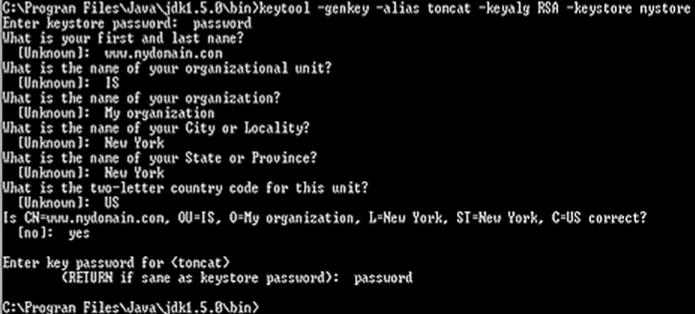
As part of a long-term effort to simplify Symantec’s product range and ensure their offerings are relevant to the latest security needs, Symantec is discontinuing (End of Life) their Symantec Safe Site product as of March 2016.
Symantec Safe Site (formally the VeriSign Trust Seal) is the stand-alone seal product which allows a user to display the seal without having to purchase an SSL certificate.
Note: There will be no impact on the Norton Secured Seal included in SSL certificate products.
Symantec Safe Site End of Life FAQ:
What should I do?
In order to continue displaying the Norton Secured Seal on their website, you will need to purchase one of our Symantec SSL products. Any Symantec Safe Site customer who chooses not to upgrade will lose their existing Symantec Safe Site at the end of their current product’s current term.
Why is Symantec discontinuing Symantec Safe Site?
Symantec want’s to simplify their product range, so they plan to eliminate smaller products that essentially have become redundant. Symantec Safe Site has been marked as a product that is not essential in their range and can be discontinued. Symantec SSL offers the same Norton Secured Seal, plus additional features that more comprehensively protect websites and simultaneously project trust.
Does this affect the seal on any other products?
No, the seal for all other products will still be available. No changes will be made.
What will happen if I don’t want another product?
Customers will not be able to renew their Symantec Safe Site product once their term is complete, so at that time they will no longer have access to the Norton Secured Seal nor Malware Scanning.
We suggest you upgrade to Symantec SSL to continue reaping the benefits you clearly value from the Norton Secured Seal, in addition to the added website security that comes with an SSL certificate.
If you currently have an SSL certificate but are not displaying the Norton Secured Seal visit our SSLSupportDesk article: Norton Secured Seal Installation Instructions
SSLSupportDesk is part of Acmetek who is a trusted advisor of security solutions and services. They provide comprehensive security solutions that include Encryption & Authentication (SSL), Endpoint Protection, Multi-factor Authentication, PKI/Digital Signing Certificates, DDOS, WAF and Malware Removal. If you are looking for security look no further. Acmetek has it all covered!
Contact an SSL Specialist to get a consultation on the Website Security Solutions that can fit your needs.
Become a Partner and create additional revenue stream while the heavy lifting for you.