Google Chrome Will Mark HTTP Sites ‘Not Secure’ from July 2018 with the Release of Chrome 68
New Highlights:
- Google Chrome will start labelling all Non HTTP sites as “Not Secure”
- The change will come with the Chrome 68 release in July 2018
- Google’s Lighthouse tool, an open source app, helps developers run audits on web pages
For the past several years, Google strongly advising webmasters (sites) to adopting HTTPS encryption. Google said that within the last year, they helped users understand that HTTP sites are not secure by gradually marking a larger subset of HTTP pages as “not secure”.
As a part of this plan Google first rolled out with Chrome 58 when Google marked all HTTP pages as “Not Secure” if the web pages having password or payment credit card fields and the second stage with Chrome 62 version when Google marked all HTTP website pages opened in a private browsing windows as “Not Secure” and beginning in July 2018 with Chrome 68 release will mark all HTTP sites as “not secure” is the final stage.
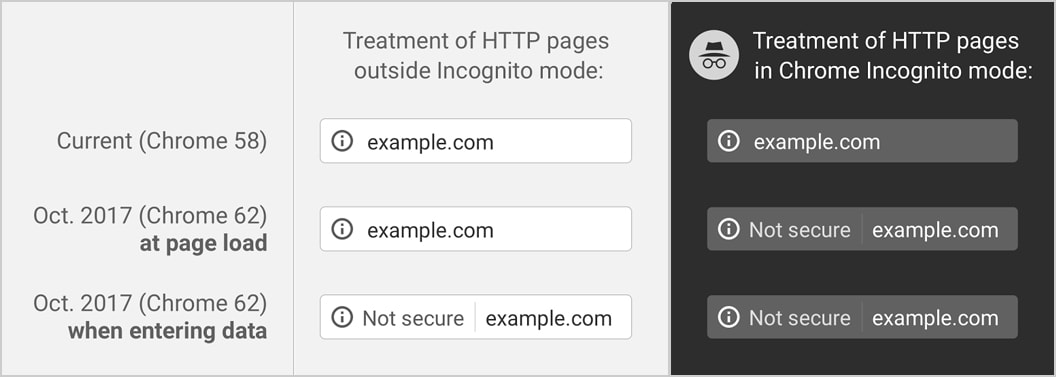
In a recent announcement, Google has confirmed that when users visit every HTTP websites on Chrome they will be flagged as “Not Secure” from July 2018 with the release of Chrome 68.
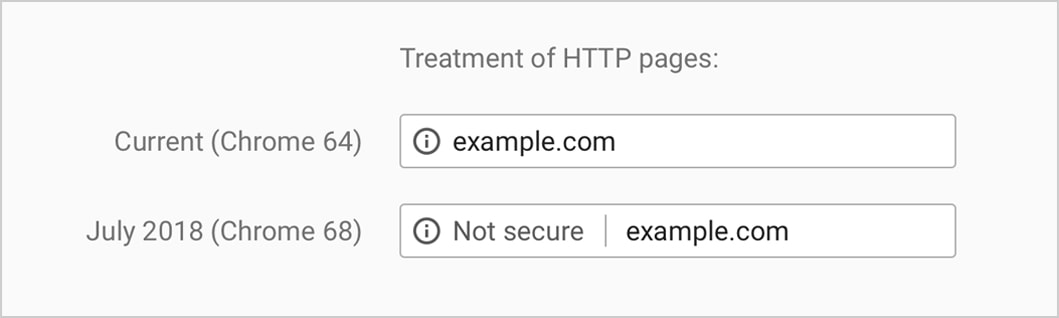
In Chrome 68, the omnibox will display “Not secure” for all HTTP pages.
Developers have clearly heard the call, according to Google, the results of the efforts have been:
- Over 68% of Chrome traffic on both Android and Windows is now protected
- Over 78% of Chrome traffic on both Chrome OS and Mac is now protected
- 81 of the top 100 sites on the web use HTTPS by default
So it’s clear that HTTPS is the wave of the future when it comes to internet security.
Google Lighthouse Tool
Google itself has a Lighthouse tool is an open-source, automated tool for improving the quality of web pages. Google encourage websites to use HTTPS with its automated Lighthouse developer tool and other set-up guides to transition over.
Take a Strategic Decision to Buying a Right SSL Certificate
Focus on choosing the right SSL Certificate for your business need. Before buying an SSL Certificate, you need to understand specific requirements to secure websites such as to protect Single Domain, Multiple Sub-Domains or Different websites. Move your website from HTTP to HTTPS with an SSL Certificate today!
If you want to know more how to protect your website and safeguard customer’s data? Please complete the form below to get more assistance from an Acmetek trusted security specialist advisor today!