WhatsApp Enables Two Factor Authentication Strengthening it’s Security.
WhatsApp is a widely popular free to use cross platform smart phone messaging application that allows users to use their phone service and wifi internet to make voice/video calls, send text messages, documents, images, gif’s, user locations, etc. Its popularity is primarily due to where data rates or roaming charges can cost an arm and a leg.

WhatsApp Inc., based in Mountain View, California, was acquired by Facebook in February 2014 for ridiculous $19.3 billion US Dollars. By February 2016, WhatsApp has a user base of over one billion, making it the most popular messaging application at the time.
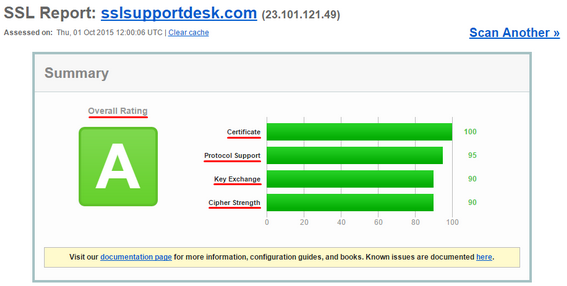
Over the recent years Privacy and Security has been a focus on the popular message app. In 2014 WhatsApp implemented end to end https encryption scrambling the information between communicating users. The latest Security implementation is the coming of Two-Step Verification.
What is Two-Step Verification?
Two-step verification is an optional feature that adds more security to your account. The technology is not new, and it has been in use for quite some time. Blizzard Inc. creator of the biggest online MMO (Massive Multiplayer Online) game World Of Warcraft implemented two factor authentication back in 2008 to protect gamers accounts from being hacked. Two-step, or Two-Factor Authentication protects your accounts by requiring you to provide an additional piece of information after you give your password In the most common implementation, after correctly entering your password, an online service will send you a text message or an email with a unique string of numbers that you’ll need to punch in to get access to your account.
Implementing Two Step Verification on WhatsApp:
To enable two-step verification, open WhatsApp > Settings > Account > Two-step verification > Enable.
Upon enabling this feature, you can also optionally enter your email address. This email address will allow WhatsApp to send you a link via email to disable two-step verification in case you ever forget your six-digit passcode, and also to help safeguard your account. WhatsApp will not verify this email address to confirm its accuracy. You will want to provide an accurate email address so that you’re not locked out of your account if you forget your passcode.
How it works..
After implementing Two-Step Verification if you receive an email to disable two-step verification, or receive a pass-code request but did not request this, do not click on the link! Someone could be attempting to verify your phone number on WhatsApp elsewhere. Meaning that someone is attempting to gain access to your account! Stay secure.
Lead Tech Engineer: Dominique Rafael
dsrafael@acmetek.com